CanCan and RailsAdmin in Ecommerce
I’ve written about Rails Admin a lot lately. One thing I haven’t written about is how it can leverage CanCan for user authorization. Once a user is authenticated via Devise, CanCan adds an additional layer for you to control how users can access and interact with data from the admin.
A Simple Example
CanCan requires that you create an Ability class where all user permissions are defined. A very basic example in RailsAdmin ecommerce context might look like this:
class Ability
include CanCan::Ability
if user && user.is_admin?
can :access, :rails_admin
can :dashboard
can :manage, [User,
Product,
Order]
end
endNote that in the above code, a user that is admin (where is_admin? returns a truthy reponse) has access to RailsAdmin, and the admin user can manage (create, read, update, destroy) all users, products, and orders.
Multi-Merchant Solution
Let’s go a little deeper. Multi-merchant solutions are a frequent request in ecommerce. Let’s say we have the following over-simplified data model, where users own and manage products and products are displayed by category:
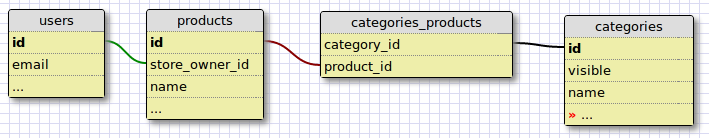
The Ability class might look like:
class Ability
include …ecommerce rails
Debugging Celery Tasks in Django Projects
I recently had the opportunity to work on a Django project that was using Celery with RabbitMQ to handle long-running server-side processing tasks. Some of the tasks took several hours to complete. The tasks had originally been executed with the at command and others had been managed with cron jobs. The client had started to migrate several of the tasks to use Celery when I joined the project.
As I started to debug the Celery tasks, I quickly discovered there were many moving parts involved and it was not immediately clear which piece of the system was the cause of the problem. I was working in a local development environment that closely matched the production system. The dev environment consisted of a virtualenv created using the same method Szymon Guz wrote about in his article Django and virtualenvwrapper. Django, Celery and their related dependencies were installed with pip and I installed RabbitMQ with Homebrew. After activating my virtualenv and starting up everything up (or so I thought), I jumped in to an IPython shell and began to debug the tasks interactively. Some tasks completed successfully but they finished almost instantaneously which didn’t seem right. The client …
django
Dealing with Rails Application Complexity — A Report from MWRC
One of the major themes coming out of the 2012 Mountain West Ruby Conference (MWRC) was the rising complexity of Ruby applications, in particular with Rails. The focus of many of the talks was directed at the pain many of us are feeling with our bloated Rails models. When I first started developing with Rails back in 2007, much of the focus was moving the application logic from the view to the controller. Then, a few years ago, the “thin controller, fat model” mantra had us all moving our code from the controller to the model. While each of these steps were an improvement, Rails developers are now dealing with what is affectionately referred to as a “stinking pile of poo” in our models.
Having seen my share of fat models of late, this topic really grabbed my interest. I started thinking about this problem a couple of months ago while working on a rather large Rails application. Thanks to some good folks in the #urug (Utah Ruby Users Group) channel on Freenode I was pointed to the article Rails is Not Your Application which got me thinking about better ways to handle unmaintainable and unapproachable models in Rails. I was happy to see that I’m not the only one thinking about …
conference ruby rails
Three Things: Startups, Rails news, jQuery index
I recently had a conversation with Jon about End Point blogging, microblogging, and tweeting. Many of us End Pointer’s have tips and tools that we encounter regularly that aren’t worthy of an entire blog post, but are worthy of sharing. Here’s my first attempt at sharing smaller bits of info – stay tuned to see how it works out.
1. Paul Graham’s Ambitious Startup
Here is an interesting recent article by Paul Graham entitled Frighteningly Ambitious Startup Ideas. It’s great. Read it.
2. Rails Vulnerability Hack
If you aren’t up to speed on things going on in the Rails world, check out this recent commit. A GitHub user was able to exploit Rails’ mass-assignment vulnerability to commit to the Rails core. Check out a few more related links at A Fresh Cup’s post on the incident.
3. jQuery’s index method
I recently came across the index method in jQuery, and wanted to share an example of its use. I’m using jQuery UI’s accordion on four categories (Period, Genre, Theme, Nationality) that have a set of options. A user can click any of the options to filter products, e.g. clicking on Folk Songs in the screenshot to the right would bring up products that have a Genre of Folk Songs. On the … |
jquery rails tips
MWRC Highlights Part 1 of 2
I attended the 2012 Mountain West Ruby Conference in Salt Lake City last week. There were a lot of cool topics presented at this conference, but I’ve been suffering serious analysis paralysis trying to pick one topic to focus on here. So, I’m taking the easy way out. I’m going to run through some of the projects and tools mentioned during the conference that I flagged in my notes to check out further.
Sidekiq, a multi-threaded drop-in replacement for Resque
- Sidekiq requires much less RAM to do the same amount of work as the single-threaded Resque, while providing a very similar API to Resque. It’s been designed to behave like Resque as much as possible and as such, would be a very easy transition for anyone that’s used Resque before.
- By Mike Perham
- Get it at: mperham.github.com/sidekiq
- Recommended by: Tony Arcieri
Book: Growing Object-Oriented Software Guided by Tests (aka GOOS)
- The “GOOS book” was recommended by a number of speakers at the conference. One downside (for me) is that the Auction Sniper app developed in the book is done in Java. However, there are now ports of that code available in Ruby, Scala, C# and Groovy. Check out the book’s website. The table of contents is …
conference ruby rails
Puppet custom facts and Ruby plugins to set a homedir
Photo of Swedish Chef by A. M. Kuchling
Puppet is an indispensable tool for system admins, but it can be tricky at times to make it work the way you need it to. One such problem one of our clients had recently was that they needed to track a file inside a user’s home directory via Puppet (a common event). However, for various reasons the user’s home directory was not the same on all the servers! As Puppet uses hard-coded paths to track files, this required the use of a custom Puppet “fact” and a helper Ruby script plugin to solve.
Normally, you can use Puppet to track a file by simply adding a file resource section to a puppet manifest. For example, we might control such a file inside a manifest named “foobar” by writing the file puppet/modules/foobar/init.pp as so:
class foobar {
user {
"postgres":
ensure => present,
managehome => true;
}
file {
"/home/postgres/.psqlrc":
ensure => present,
owner => postgres,
group => postgres,
mode => 644,
source => [
"puppet:///foobar/$pg_environment/psqlrc", …automation ruby sysadmin
Liquid Galaxy in GSoC 2012!
Once again The Liquid Galaxy Project has been accepted for the Google Summer of Code! Google Summer of Code is a tremendous program that provides an excellent opportunity for talented undergraduate and graduate students to work developing Open Source software guided by a mentor. Students receive $5000 stipends for successfully completing their summer projects. Last year The Liquid Galaxy Project had three GSoC slots for students. This year we are hoping for at least this number of slots again. I know it is not the point, but did I mention that participation in the program is a very nice credit for students to have on their resumes? ;-)
Right now we are in the “would-be student participants discuss application ideas with mentoring organizations” phase of the program. Interested students should contact the project’s mentors and admins by emailing lg-gsoc@endpoint.com or by jumping into the #liquid-galaxy Freenode IRC channel. Applicants are well advised to take advantage of the opportunity to consult with project mentors in developing their applications. Student applications are being accepted until April 6 and should be emailed to lg-gsoc@endpoint.com.
The Liquid Galaxy GSoC 2012 …
visionport open-source
Firebug in Action: CSS Changes
When I work with clients, I encourage them to use tools to improve efficiency for web development. Sometimes my clients want styling (CSS) adjustments like font-size, padding, or orientation changes, but they aren’t sure what they want before they’ve seen it applied to real content. I recommend embracing a tool such as Firebug for examining temporary on-page CSS edits. Here’s a quick video that demonstrates Firebug in action as I try out a few adjustments to End Point’s home page.
Some of the changes I test out in the video include:
- Font-color changes
- Deleting DOM elements
- Padding, margin adjustments
- Background color changes
Firebug offers a lot more functionality but the video covers interactive CSS changes only. Read more about Firebug’s features here. Chrome has similar functionality with the Developer Tools included in the core software. There are similar tools in the other browsers, but I develop in Chrome or Firefox and I’m not familiar with them.
css tips tools






