Slony: Cascading Subscriptions
Sometime you run into a situation where you need to replicate one dataset to many machines in multiple datacenters, with different costs associated with sending to each (either real costs as in bandwidth, or virtual costs as in the amount of time it takes to transmit to each machine). Defining a Slony cluster to handle this is easy, as you can specify the topology and paths taken to replicate any changes.
Basic topology:
- Data center A, with machines A1, A2, A3, and A4.
- Data center B, with machines B1, B2, B3, and B4.
- Data center C, with machines C1, C2, C3, and C4.
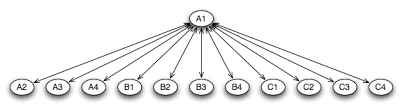
Figure 1: Non-cascaded slony replication nodes/pathways.
Node A1 is the master, which propagates its changes to all other machines. In the simple setup, A1 would push all of its changes to each node, however if data centers B and C have high costs associated with transfer to the nodes, you end up transferring 4x the data needed for each data center. (We are assuming that traffic on the local subnet at each data center is cheap and fast.)
The basic idea then, is to push the changes only once to each datacenter, and let the “master” machine in the data center push the changes out to the others in the data center. This …
postgres scalability
Blog versus Forum, Blogger versus WordPress in Ecommerce

Today, Chris sent me an email with two questions for one of our ecommerce clients:
- For ecommerce client A, should a forum or blog be added?
- For ecommerce client A, should the client use Blogger or WordPress if they add a blog?
These are relevant questions to all of our clients because forums and blogs can provide value to a static site or ecommerce site. I answered Chris’ question and thought I’d expand on it a bit for a brief article.
First, a rundown comparing the pros and cons of blog versus forum:
| Blog | Forum | |
| Pros |
|
|
| Cons |
|
|
ecommerce seo
SEO 2010 Trends and Strategies
Yesterday I attended SEOmoz’s webinar titled “SEO Strategies for 2010”. Some interesting factoids, comments and resources for SEO in 2010 were presented that I thought I’d highlight:
-
Mobile browser search
- Mobile search and ecommerce will be a large area of growth in 2010.
- Google Webmaster Tools allows you to submit mobile sitemaps, which can help battle duplicate content between non-mobile and mobile versions of site content. Another way to handle duplicate content would be to write semantic HTML that allows sites to serve non-mobile and mobile CSS.
-
Social Media: Real Time Search
- Real time search marked its presence in 2009. The involvement of Twitter in search is evolving.
- Tracking and monitoring on URL shortening services should be set up to measure traffic and benefit from Twitter.
- Dan Zarrella published research on The Science of Retweeting. This is an interesting resource with fascinating statistics on retweets.
-
Social Media: Facebook’s Dominance
- Recent research by comScore has shown that 5.5% of all time on the web is spent in Facebook.
- Facebook has very affordable advertising. Facebook has so much demographic and psychographic data that allows sites to deliver …
ecommerce seo
Splitting Postgres pg_dump into pre and post data files
I’ve just released a small Perl script that has helped me solve a specific problem with Postgres dump files. When you use pg_dump or pg_dumpall, it outputs things in the following order, per database:
- schema creation commands (e.g. CREATE TABLE)1. data loading command (e.g. COPY tablename FROM STDIN)1. post-data schema commands (e.g. CREATE INDEX)
The problem is that using the –schema-only flag outputs the first and third sections into a single file. Hence, if you load the file and then load a separate –data-only dump, it can be very slow as all the constraints, indexes, and triggers are already in place. The split_postgres_dump script breaks the dump file into two segments, a “pre” and a “post”. (It doesn’t handle a file with a data section yet, only a –schema-only version)
Why would you need to do this instead of just using a full dump? Some reasons I’ve found include:
- When you need to load the data more than once, such as debugging a data load error.
- When you want to stop after the data load step (which you can’t do with a full dump)
- When you need to make adjustments to the schema before the data is loaded (seen quite a bit on major version upgrades)
Usage …
database open-source perl postgres
Gathering server information with boxinfo
I’ve just publicly released another Postgres-related script, this one called “boxinfo”. Basically, it gathers information about a box (server), hence the catchy and original name. It outputs the information it finds into an HTML page, or into a MediaWiki formatted page.
The goal of boxinfo is to have a simple, single script that quickly gathers important information about a server into a web page, so that you can get a quick overview of what is installed on the server and how things are configured. It’s also useful as a reference page when you are trying to remember which server was it that had Bucardo version 4.5.0 installed and was running pgbouncer.
As we use MediaWiki internally here at End Point (running with a Postgres backend, naturally), the original (and default) format is HTML with some MediaWiki specific items inside of it.
Because it is meant to run on a wide a range of boxes as possible, it’s written in Perl. While we’ve run into a few boxes over the years that did not have Perl installed, the number that had any other language you choose (except perhaps sh) is much greater. It requires no other Perl modules, and simply makes a lot of system calls.
Various information …
database mysql open-source perl postgres
Rails Ecommerce with Spree: Customizing with Hooks Comments
Yesterday, I went through some examples using hook and theme implementation in Spree, an open source Ruby on Rails ecommerce platform. I decided to follow-up with closing thoughts and comments today.
I only spent a few hours working with the new Spree edge code (Version 0.9.5), but I was relatively happy with the Spree theme and hook implementation, as it does a better job decoupling the extension views with Spree core functionality and views. However, I found several issues that are potential areas for improvement with this release or releases to come.
Theme too clunky?
One concern I have is that the entire “views” directory from SPREE_ROOT/app was moved into the theme with this theme-hook work (all of the “V” in MVC). Yesterday, I discussed how WordPress had designed a successful theme and plugin interaction and one thing I mentioned was that a WordPress theme was lightweight and comprised of several customer-facing PHP files (index, single post page, archive pages, search result page). Moving all of the Spree core views to the theme presents a couple of issues, in my opinion:
- A developer that jumps into theme development is immediately met with more than 50 files in the theme …
rails spree
Rails Ecommerce with Spree: Customizing with Hooks Tutorial
In the last couple months, there’s been a bit of buzz around theme and hook implementation in Spree. The Spree team hasn’t officially announced the newest version 0.9.5, but the edge code is available and developers have been encouraged to work with the edge code to check out the new features. Additionally, there is decent documentation about theme and hook implementation. In this article, I’ll go through several examples of how I would approach site customization using hooks in the upcoming Spree 0.9.5 release.
Background
I’ve been a big proponent of how WordPress implements themes, plugins, and hooks in the spree-user Google group. The idea behind WordPress themes is that a theme includes a set of PHP files that contain the display logic, HTML, and CSS for the customer-facing pages:
- index
- a post page
- archive pages (monthly, category, tag archives)
- search result page
- etc.
In many cases, themes include sections (referred to as partial views in Rails), or components that are included in multiple template pages. An example of this partial view is the sidebar that is likely to be included in all of the page types mentioned above. The WordPress theme community is abundant; there are …
ecommerce rails spree
Postgres Upgrades — Ten Problems and Solutions
Upgrading between major versions of Postgres is a fairly straightforward affair, but Murphy’s law often gets in the way. Here at End Point we perform a lot of upgrades, and the following list explains some of the problems that come up, either during the upgrade itself, or afterwards.
When we say upgrade, we mean going from an older major version to a newer major version. We’ve (recently) migrated client systems as old as 7.2 to as new as 8.4. The canonical way to perform such an upgrade is to simply do:
pg_dumpall -h oldsystem > dumpfile
psql -h newsystem -f dumpfileThe reality can be a little more complicated. Here are the top ten gotchas we’ve come across, and their solutions. The more common and severe problems are at the top.
1. Removal of implicit casting
Postgres 8.3 removed many of the “implicit casts”, meaning that many queries that used to work on previous versions now gave an error. This was a pretty severe regression, and while it is technically correct to not have them, the sudden removal of these casts has caused lots of problems. Basically, if you are going from any version of PostgreSQL 8.2 or lower to any version 8.3 or higher, expect to run into …
database postgres tips



