End Point Featured as Global Leader in Ruby on Rails & Ecommerce Development

As the year comes to a close and we reflect on the goals we’ve accomplished and the work that made it all possible, we are proud to announce our inclusion on the Clutch Global Leaders List, encapsulating the 475+ most highly reviewed companies from around the world. We placed as a leader on both Top Ruby on Rails Developers and Top Ecommerce Developers, being the best New York-based firm on the former and in the top three from New York on the latter.
Achieving the status of a Clutch Global Leader in not just one, but two categories speaks volumes on the effort we’ve put forth in 2017. We couldn’t have hit this milestone without skilled work from End Point staff and the great relationships we’ve nurtured with clients. Looking back on these memorable projects, here are some of the things are clients wrote on our Clutch profile:
“I’ve worked with a lot of different service providers. Results can vary across the board. End Point is very transparent about what they’re working on in terms of providing complete details. We don’t have any surprises at the end of the month as a result. They’re very dependable, delivering what they promise every time,” explained the Director of Ecommerce …
company ruby rails ecommerce
Mobile Device and Application Management (MAM vs. MDM)
Businesses of all sizes have been increasingly using mobile devices for all kinds of activities. Some of these activities are pretty common, like being able to read and respond to work email and manage work calendars. On the other hand, some companies are using mobile devices for more specific niche activities like checking in customers, using device cameras to read barcodes and UPC stickers, or even temporarily storing sensitive business related data.
As a result of the proliferation of mobile devices for work use, corporations and smaller businesses are finding the need the exhibit finer control over how their employees and customers use their devices. This is where mobile device management (MDM) and mobile application management (MAM) really shine and help solve many of these types of problems.
What is MDM?
Mobile device management (MDM) is a software solution that allows organizations to manage the maintenance, deployment, and configuration of mobile devices that are issued to members of the organization. All of this magic tends to be done via a store or portal application that users download onto their devices.
The app begins an enrollment process when the user enters their …
mobile android ios security
Reconciling Android source code
Recently, a client came to us with an interesting problem. They needed some changes made to an internal-use Android app that had been created for them by another company, but they didn’t have up-to-date source code for the app, and they had no way of getting it. They gave us an old archive of source code, a more recent working build of the app, and asked us to figure it out.
The working version of the app they sent us was built in early 2016, and the app was compiled for Android SDK version 22, which is 5.1 Lollipop. It came out in March 2015, so it was a year old even when the app was created, and the code was using lots of features which have since been deprecated.
After putting this source code in a Git repository, I started by building the app from the source they’d sent and comparing it to the working version. It looked mostly the same, but a couple of features were broken. At the suggestion of a coworker, I used BytecodeViewer to decompile the APK and took a look around.
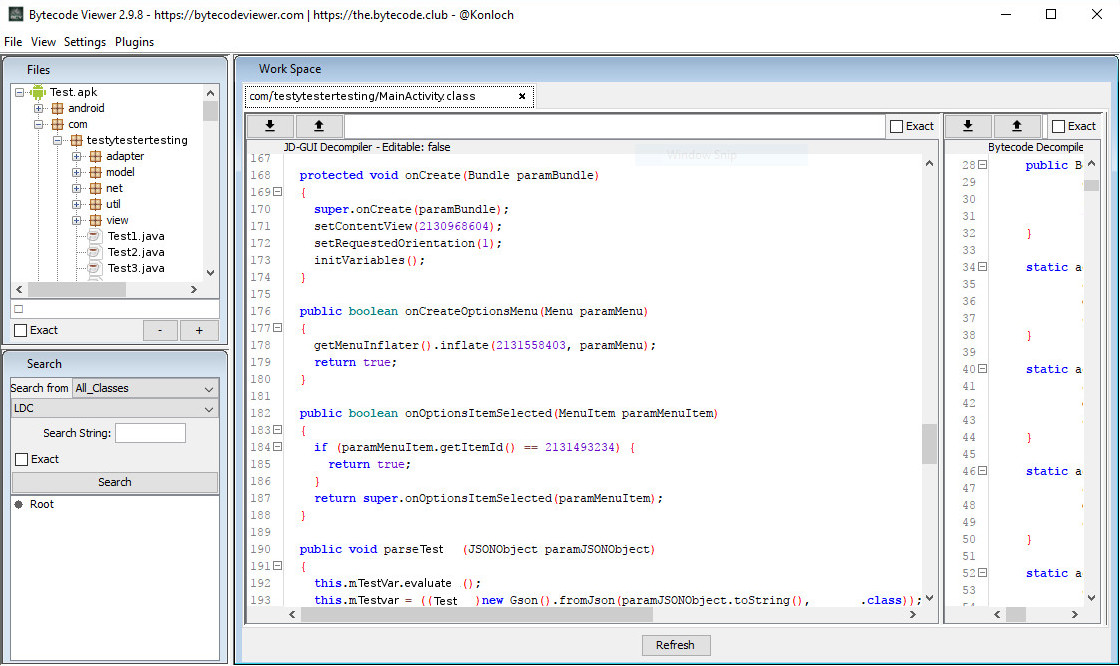
It was a little while before I was able to find any differences between the source we had and this decompiled code, but I did find a few logic differences. The source was also using a few old APIs that …
android software
Symantec Certificate Distrust (CertQuake)
If you are accustomed to running your browser with the “developer tools” panel open (which probably indicates you are a web developer), you may have seen it show the following message:
The certificate used to load https://www.example.com/ uses an SSL certificate that will be distrusted in an upcoming release of Chrome. Once distrusted, users will be prevented from loading this resource. See https://g.co/chrome/symantecpkicerts for more information.
What’s this all about? Glad you asked.
The Root of All Certificates (well, most)
Symantec is a company that operated a “PKI” (Public Key Infrastructure) business. As a Certificate Authority, they would dole out digital certificates to requestors.
Certified
These certificates are used to secure the communication we have with websites. When a site uses a certificate correctly, you will see the leading part of the URL begin with https:// (known as the protocol), and the “green-lock” icon in your browser.
Certificates can also be issued with more stringent requirements on the company obtaining them, where they must verify their company by providing articles of incorporation, etc. These are known as “EV” (Extended Validation) certs, and …
tls security browsers chrome
HGCI Summit Conference 2017, Malaysia: A conference on cloud, security and big data
I was asked by a friend to give a talk in the HGCI Summit conference on November 28th, 2017. This conference is meant to bridge the academic world and industry via knowledge and experience sharing, focusing on big data and cloud topics. It took place in the Center of Advanced Professional Education (CAPE), a center under the Universiti Teknologi Petronas (UTP) which has its main campus in Tronoh, Perak, Malaysia.
I will highlight several tracks which I attended.
Forum
On the first day, several faculty members sat together within a forum in which they discussed the main issues academics face when they need access to high performance computing. An audience member shared her experience completing her research group’s work which took very long to be rendered, while she could do it in a day when she submitted the work in a university in the US. One of the forum’s members then replied she could always work collaboratively with the other universities, and he (the forum member) offered his university’s facilities to be used for her research. Inter-varsity network bandwidth was also discussed in the forum.
Dr. Izzatdin

An interesting talk which I attended was delivered by Dr. Izzatdin from …
conference cloud security
Inserting lots of data efficiently in Rails + PostgreSQL
This is going to be a very short post about a simple solution to the problem of inserting data fast when you really have a lot of it.
The problem
For the sake of having some example to think about, imagine building an app for managing nests of ants.
You can have thousands of nests with hundreds of thousands of ants in each one of them.
To make the fun example applicable for this blog post, imagine that you’re reading data files coming from a miraculous device that “scans” nests for ants and gives you info about every ant with lots of details. This means that creation of the nest is about providing a name, coordinates, and the data file. The result should be a new nest and hundreds of thousands of ant records in the database.
How do we insert this much data without hitting the browser’s timeout?
Approaching the problem
Regular INSERT statements provide a lot of flexibility that is normally much needed, but is relatively slow. For this reason doing many of them isn’t preferred among database experts for pre-populating databases.
The solution that is typically used instead (apart from the case in which a database needs to be restored, with pg_restore having no contenders in terms of …
rails postgres
Conference Recap: PyCon Asia Pacific (APAC) 2017 in Kuala Lumpur, Malaysia
I got a chance to attend the annual PyCon APAC 2017 (Python Conference, Asia Pacific) which was hosted in my homeland, Malaysia. In previous years, Python conferences in Malaysia were held at the national level and this year the Malaysia’s PyCon committee worked hard on organizing a broader Asia-level regional conference.
Highlights from Day 1
The first day of the conference began with a keynote delivered by Luis Miguel Sanchez, the founder of SGX Analytics, a New York City-based data science/data strategy advisory firm. Luis shared thoughts about the advancement of artificial intelligence and machine learning in many aspects, including demonstrations of automated music generation. In his talk Luis presented his application which composed a song using his AI algorithm. He also told us a bit on the legal aspect of the music produced by his algorithm.

Luis speaking to the the audience. Photo from PyCon’s Flickr.
Then I attended Amir Othman’s talk which discussed the data mining technique of news in the Malay and German languages (he received his education at a German tertiary institution). His discussion included the verification of the source of the news and the issue of the …
conference python
Logstash: Removing fields with empty values
The Elastic stack is a nice toolkit for collecting, transporting, transforming, aggregating, searching, and reporting on log data from many sources. It was formerly known as the ELK stack, after its main components Elasticsearch, Logstash, and Kibana, but with the addition of Beats and other tools, the company now calls it simply the Elastic stack.
We are using it in a common configuration, on a central log server that receives logs via rsyslog over TLS, which are then stored in local files and processed further by Logstash.
When conservation is recommended
When forwarding logs on to SaaS log services such as Logentries, SumoLogic, etc., we have a limited amount of data transfer and storage allotted to us. So we need to either economize on what we send them, pay for a more expensive plan, or retain a shorter period of history.
For some very busy logs (nginx logs in JSON format) we decided to delete fields with empty values from the log event during the filter phase in Logstash. This removes a lot of data from the log message we send to the log service over the wire, and reduces the size of each log event stored in their system.
I expected this to be simple, but that expectation …
hosting logging






